Unveiling the Lazarus Threat: A Targeted Assault on South Korean Industries
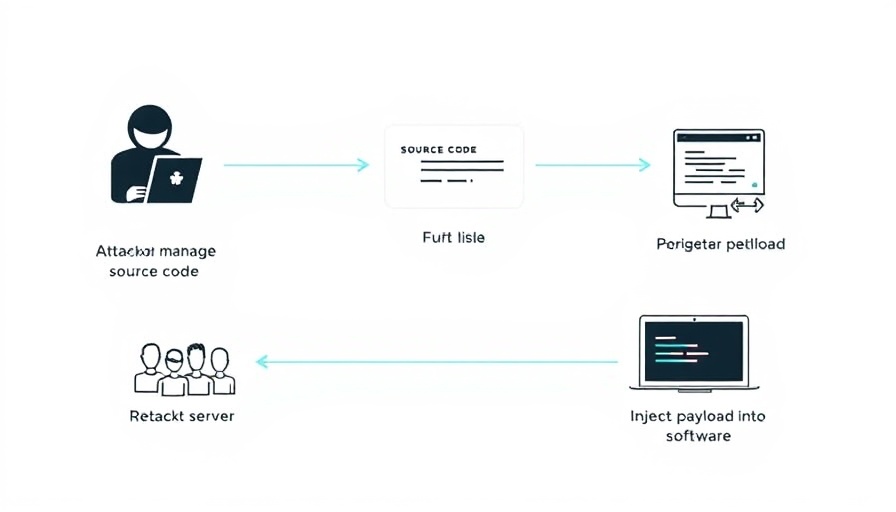
The North Korea-linked Lazarus Group has struck again, targeting at least six organizations in South Korea within several critical sectors, including software, IT, and telecommunications. Dubbed Operation SyncHole, the attack signifies the escalating sophistication of cyber threats and the challenges they pose to essential services.
Understanding the Attack Mechanism
According to experts from Kaspersky, this offensive employs a tactical blend of watering hole strategies and vulnerability exploitation. A critical point of infiltration was identified through a flaw in Innorix Agent, a software used for task automation and file transfers. Researchers noted that the Lazarus Group capitalized on a rapid vulnerability in this software to facilitate lateral movement within affected organizations.
The Role of Cross EX in Cybersecurity Vulnerabilities
Another pivotal element of this campaign is the security vulnerability found in Cross EX, a legitimate software widely utilized in South Korea for online banking. This vulnerability is uniquely alarming; it underscores how cybercriminals have adeptly manipulated trusted applications to launch attacks. As researchers delved into this, it became evident that Lazarus utilized sophisticated redirect techniques to target specific users visiting South Korean media sites, eventually leading them to malicious domains where malware was deployed.
What Lies Ahead: The Future of Cybersecurity?
As cyber threats like those posed by Lazarus continue to evolve, it is crucial for organizations to bolster their cybersecurity measures. Rapid responses to emerging vulnerabilities and an increased focus on security training for employees can prevent infiltration from groups adept at exploiting weaknesses in software. As evidenced by this incident, understanding the tactics used by adversaries like Lazarus can equip organizations to face the future more resiliently.



Write A Comment