The Alarming Rise of Malicious Browser Extensions
In an unsettling revelation, cybersecurity researchers have reported a significant wave of malware infections linked to malicious browser extensions across Latin America, particularly targeting Brazil since the start of 2025. The hacking campaign, dubbed Operation Phantom Enigma, has reportedly compromised 722 users, raising concerns among tech-savvy individuals and businesses alike.
Phishing-Based Strategy: A Closer Look
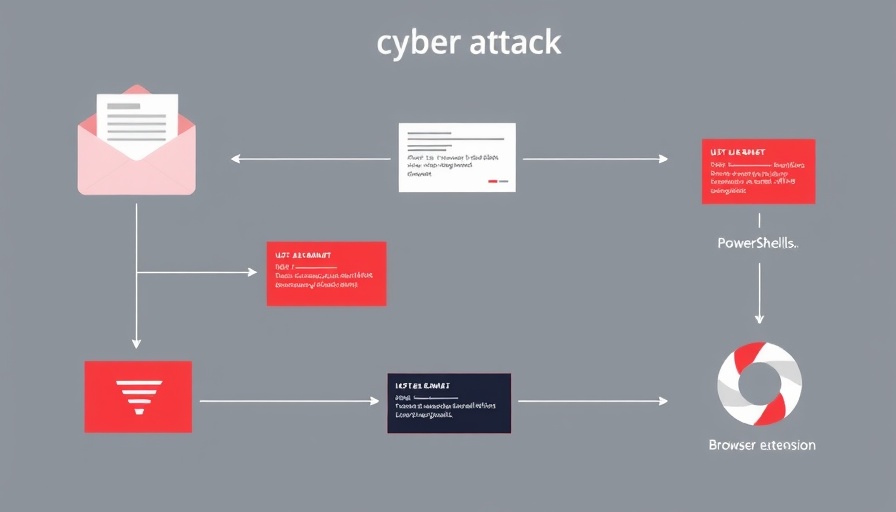
The infiltration process begins with cleverly crafted phishing emails that masquerade as legitimate invoices. These deceptive communications urge recipients to download harmful attachments or click on embedded links. As reported, certain phishing emails even appear to originate from compromised corporate servers, thereby increasing the likelihood of user engagement.
Technical Intricacies Behind the Attack
At the heart of this devious plot is a sophisticated multi-stage process initiated by a batch script. This script downloads a subsequent PowerShell script designed to check various system configurations, such as the presence of security software designed to protect online banking transactions in Brazil. Through disabling User Account Control (UAC) and establishing persistent access, the attackers ensure a long-term foothold on the compromised machines.
Impact on Banking Security
Among the notable features of the malicious extension is its ability to execute JavaScript code targeted at banking websites, including Banco do Brasil. This capability underscores a troubling trend where cybercriminals are leveraging increasingly sophisticated avenues to harvest sensitive user authentication data.
Global Implications and Prevention Strategies
While the majority of the victims have been located in Brazil and Colombia, other countries including Mexico and the Czech Republic have been affected. The infiltration of malware on a global scale accentuates the need for heightened cybersecurity awareness. Users are urged to be vigilant: ensuring their systems are updated, employing quality cybersecurity software, and refraining from downloading extensions from untrusted sources.
Establishing Cyber Hygiene Practices
With the rapid evolution of cyber threats, maintaining strong cyber hygiene practices is crucial. Regular training and awareness campaigns can help fortify the defenses of individuals and businesses against such malicious acts.
As the landscape of cybersecurity continues to evolve, staying informed about emerging threats and implementing proactive measures are essential for protecting personal and organizational data against cybercriminals.



Write A Comment